.
Let's take a look at a few configuration files and all the important parameters to configure in each file.
Apache2.conf
The first file we are going to configure is apache2.conf which is located in the following path: /etc/apache2/apache2.conf. It is the most important file in Apache, since it will define the general behaviour of the web server and it is also responsible for accessing the different modules that extend the server's functionality.
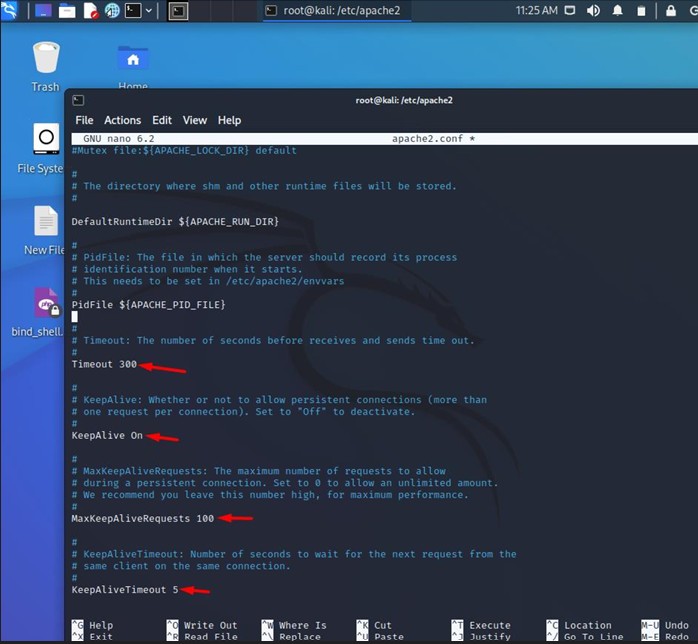
Timeout
This directive determines how long the server waits for the client.
- Default value: 300. This means that the timeout time for the server to wait for the client is 300 seconds.
- Possible values: As long as desired. The longer you set, the longer the waiting time between the server and the client, the more prone we are to DoS attacks and the slower the server will be to cut connections.
- Recommended value: The recommended value varies depending on the website. The recommended value is between 10 and 60 seconds at most. Since, if the waiting time between the server and the client is shorter, it would help to not saturate the server so much and mitigate DoS attacks.
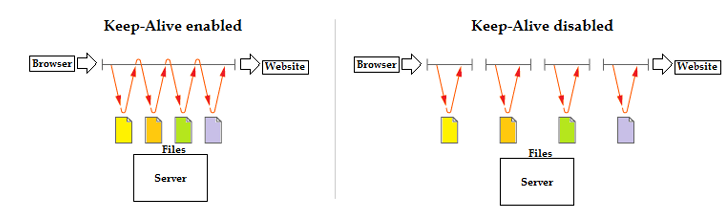
KeepAlive.
Determines whether or not the client is allowed to make multiple connections to the server. KeepAlive can be used to prevent a client from consuming too many server resources.
- Default value: On. This means if set to "On", it will provide long-running HTTP sessions that allow multiple requests to be sent over the same TCP connection.
- Possible values: On or Off. If left On, if a server needs to respond to multiple HTTP requests simultaneously and serve a single file for each new TCP connection, the page load time of the site will increase. This can lead to a bad user experience.
- Recommended value: As a security recommendation it is better to leave it on Off as leaving it On will increase the load time and make it more prone to DoS attacks.
KeepAliveRequests
Limits the number of requests allowed per connection from a client. It is used to control persistent connections.
- Default value: 100. This means that 100 requests will be allowed per client connection.
- Possible values: As many as possible. If set to 0, unlimited requests will be allowed. The higher the value set, the more requests a client will be able to make and the more prone the server will be to saturation and DoS attacks.
- Recommended value: Depends on each application. The recommended value is between 50 and 75.
KeepAliveTimeout
Amount of time the server will wait for subsequent requests on a persistent connection.
- Default value: 5. The Apache server will wait 5 seconds for a subsequent request before closing the connection.
- Possible values: As long as possible. Setting a high value may cause performance problems on heavily loaded servers. The longer the timeout, the more server processes will be kept busy waiting for connections with idle clients.
- Recommended value: Depends on the application. It is best to set the value as low as possible as this will make the server run smoother and less prone to DoS attacks
Security.conf
This file is located in the /etc/apache2/conf-available directory. In this file there are several directives for the security of our apache. It is very important when hardening our server.
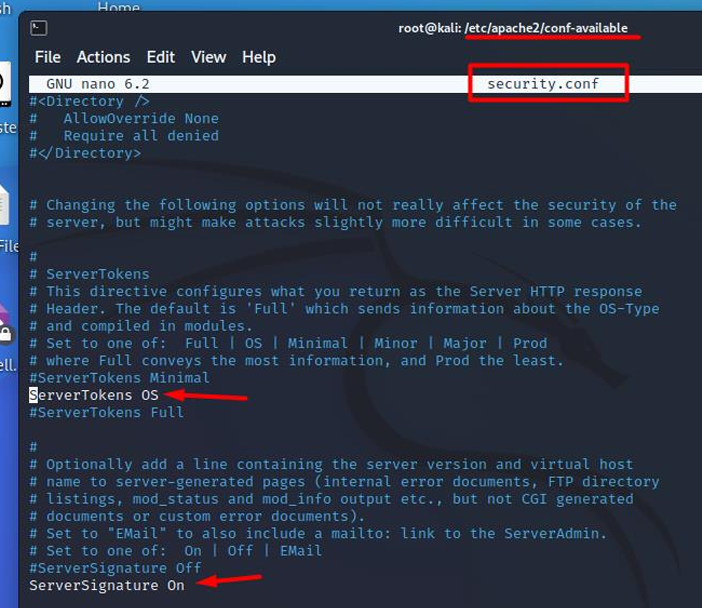
ServerTokens
This directive controls whether the (Server)response header field sent to clients includes a description of the server's generic operating system type, as well as information about compiled modules.
This directive controls whether the (Server)response header field sent to clients includes a description of the server's generic operating system type, as well as information about compiled modules.
- Default value: OS. This means that the server sends, for example :Server: Apache/2.4.1 (Unix).
- Possible values:
- Major: The server sends, for example :Server: Apache/2.
- Minor: Server sends, for example :Server: Apache/2.4
- Min[imal]: Server sends, for example :Server: Apache/2.4.1
- Full: Server sends, for example :Server: Apache/2.4.1 (Unix) PHP/4.2.2 MyMod/1.2
- Proud: Server sends, for example :Server: Apache.
- Recommended value: The recommended value would be to configure it with the "Proud" parameter, as it will not show the version of our Apache. This would prevent cybercriminals from knowing the version of our apache and complicate the hacking attempt.
ServerSignature
Allows the configuration of a footer line at the end of the documents generated by the server (error messages, mod_proxy, ftp directory listings, mod_info, output, ...). The reason why you would want to enable such a footer is that in a chain of proxies, the user often has no way of knowing which of the chained servers actually produced a returned error message.
- Default value: On. When set to ‘On’, it is allowed to be displayed at the bottom of the pages generated by Apache, for example, when displaying error 404 (document not found).
- Possible values:
- On: Simply adds a line with the server version number and ServerName of the virtual service host
- Off: Suppresses the footer line (and is therefore compatible with the behaviour of Apache-1.2 and earlier versions)
- Email: Also creates a "mailto:" reference to the ServerAdmin document being referenced.
- Recommended value: The recommended value would be "Off", so we suppress the footer and do not give extra information about our browser.
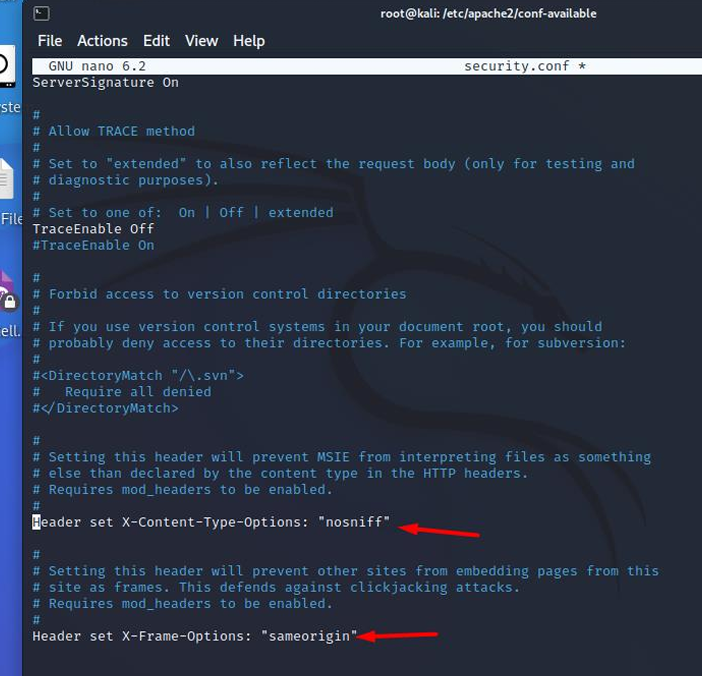
Header set X-Content-Type-Options
It is used to protect against MIME detection vulnerabilities. These vulnerabilities can occur when a website allows users to upload content to a website, however, the user disguises a particular file type as something else. This can give them the opportunity to perform cross-site scripting and compromise the website.
- Default value: "nosniff", browsers that support this header (IE and Chrome), will not load stylesheets, or scripts (Javascript), whose Myme-type is not appropriate.
- Possible values:
- Recommended value: The recommended value would be the default "nosniff", as this security header helps prevent this type of attack by disabling the MIME detection functionality of IE and Chrome browsers so that the browser must use the MIME type sent through the origin server.
Header set X-Frame-Options
It can be used to indicate whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed> or <object>. Web pages can use it to avoid click-jacking attacks by ensuring that their content is not embedded on other sites.
- Default value: "sameorigin", This means that you can use the page in a frame as long as the site that includes it is the same one that serves it.
- Possible values:
- Sameorigin: The page can be used in a frame as long as the site that includes it is the same one that serves it.
- Deny: The page cannot be displayed in a frame, independent of the site that is trying to display it
- ALLOW-FROM uri: This is an obsolete directive that no longer works in modern browsers. Do not use. In older browser support, a page can be displayed in a frame only at the specified source uri.
- Recommended value: The recommended value would be the default "Sameorigin", as we will have protection against ClickJacking, which is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when trying to click on the top level page.
PHP.ini
This file is located in the path /etc/php/8.1/cli/php.ini. Php.ini is a file that allows us to adjust the configuration of PHP.
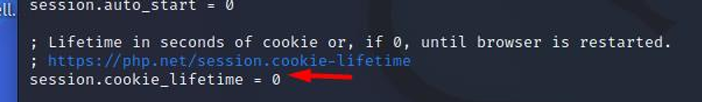
Session.cookie_lifetime
Specifies the lifetime in seconds of the cookie that is sent to the browser.
- Default value: "0", The value 0 means "until the browser closes".
- Recommended value: The recommended value would be the default "0", since when a browser terminates, the session ID cookie is immediately deleted.
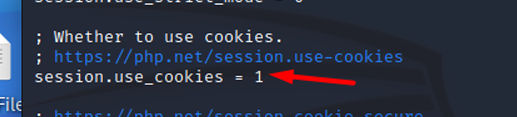
Session.use_cookies
Specifies whether the module will use cookies to store the session id on the client side.
- Default value: "1", This means that cookies are allowed to be used to store the session id on the client side.
- Possible values:
- Recommended value: The recommended value varies from website to website. But it is safest to set it to ‘0’.
Session.use_only_cookies
Specifies whether the module will only use cookies to store the session id on the client side. Enabling this setting prevents attacks that involve passing the session id in the URL.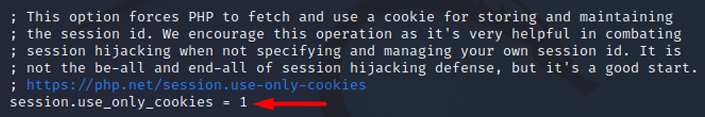
- Default value: "1", This means that cookies are allowed to be used to store the session id on the client side.
- Possible values:
- Recommended value: The recommended value is "1", as enabling this setting prevents attacks that involve passing the session id in the URL.
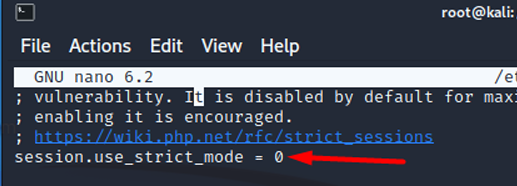
session.use_strict_mode
Prevents the session module from using uninitialised session IDs. In other words, the session module only accepts valid session IDs generated by itself. Rejects session IDs provided by users. Session ID injection could be performed through cookie injections via JavaScript on a permanent or temporary basis.
- Default value: "0", This means that it is disabled.
- Possible values:
- Recommended value: It is mandatory to enable session.use_strict_mode for general session security. All sites are warned about this.
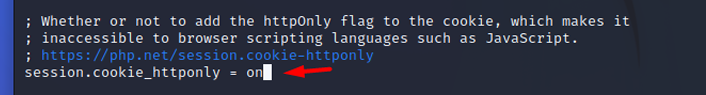
session.cookie_httponly
Marks the cookie as accessible only through the HTTP protocol. This means that the cookie will not be accessible by scripting languages, such as JavaScript. This setting can effectively help to reduce identity theft through attacks (although it is not supported by all browsers).
- Default value: "on", This means that JavaScript is denied access to session cookies.
- Possible values:
- On: Enabled
- Off: Disabled
- Recommended value: The recommended value would be the default ‘On’, as this setting prevents cookie theft by JavaScript injections. It is possible to use session IDs as CSRF protection keys, although this is not recommended. For example, HTML source code could be saved and sent to other users. For security, developers should not write session IDs in web pages. Almost all applications should use the httponly attribute for session ID cookies.
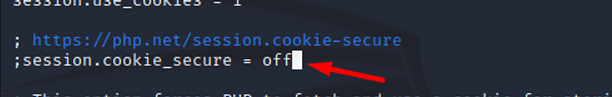
session.cookie_secure
Specifies whether cookies should only be sent over secure connections.
- Default value: "Off", This means that cookies can be sent on both secure and non-secure connections.
- Possible values:
- Recommended value: The recommended value would be ‘On’, as if a website is an HTTPS-only site, this setting should be enabled. HSTS should not be considered for HTTPS-only websites.
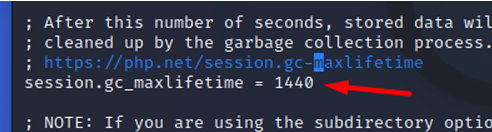
session.gc_maxlifetime
Specifies the number of seconds after which data is seen as “rubbish” and potentially cleaned up. Rubbish collection can happen during session startup.
- Recommended value: “1440”, This means that there are 1440 seconds before the information is seen as rubbish and deleted.
- Recommended value: As many seconds as desired.
- Recommended value: The recommended value would be the smallest possible value so that obsolete sessions are deleted with appropriate frequency. If auto-identification is required, a secure auto-identification feature has to be implemented. Do not use long-lived session IDs for this purpose.
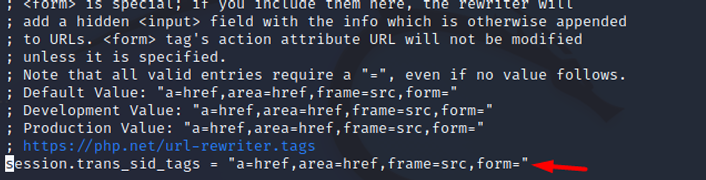
session.use_trans_sid
Specifies which HTML tags are rewritten to include the session ID when transparent SID support is enabled.
- Recommended value: “a=href,area=href,frame=src,input=src,form= form”, is a special label. <input hidden="id_sesión" name="session_name"> is added as a form variable.
- Possible values:
- Off
- a=href,area=href,frame=src,input=src,form= form
- Recommended value: The recommended value would be ‘Off’, as it would improve overall session ID security by eliminating the possibility of session ID injections and leaks.
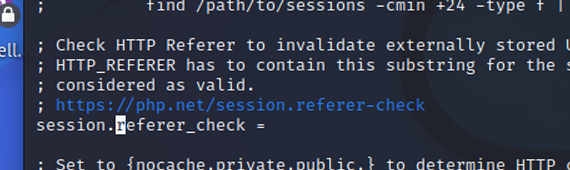
session.referer_check
Contains the substring to check each HTTP Referer. If the Referer was sent by the client and the substring was not found, the embedded session id will be marked as invalid.
- Default value: “Empty string”, This means that the page can be used in a frame as long as the site that includes it is the same one that serves it.
- Possible values:
- Recommended value: When session.use_trans_sid is enabled, it is recommended to use this setting if possible. It reduces the risk of session ID injections. If a site outside http://example.com/, is to be set up http://example.com/ for that purpose. Note that, when using HTTPS, browsers will not send the recommended header. Browsers may not send the header due to their configuration. Therefore, this setting is not a trusted security measure.
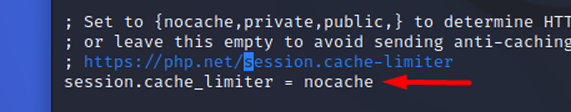
session.cache_limiter
Specifies the cache control method used by session pages.
- Recommended value: “nocache”, This means that it ensures that HTTP content is not cached for authenticated sessions. It allows caching only when the content is not private. Otherwise, the content could be exposed.
- Possible values:
- Nocache: Ensures that HTTP content is not cached for authenticated sessions.
- Private: "private" could be used if the HTTP content does not include security-sensitive data. Note that "private" may leave private data cached by shared clients.
- Private_no_expire: The cache does not expire.
- Public: "public" may be used only when the HTTP content does not contain any private data at all.
- Recommended value: The recommended value would be the default ‘nocache’, as it ensures that HTTP content is not cached for authenticated sessions.
session.hash_function
Allows you to specify the hashing algorithm used to generate the session IDs.
- Default value: (Does not appear).
- Possible values:
- 0: Means MD5 (128 bits)
- 1: Means SHA-1 (160 bits).
- Recommended value: The recommended value would be ‘1’, as the SHA-1 algorithm is more secure than MD5.
There are many more parameters to configure, but these will be the most important when securing the Apache. Each of them provides some mitigation of possible attacks on our server.